Samsung Lets Out Smart Things app source code and secret keys
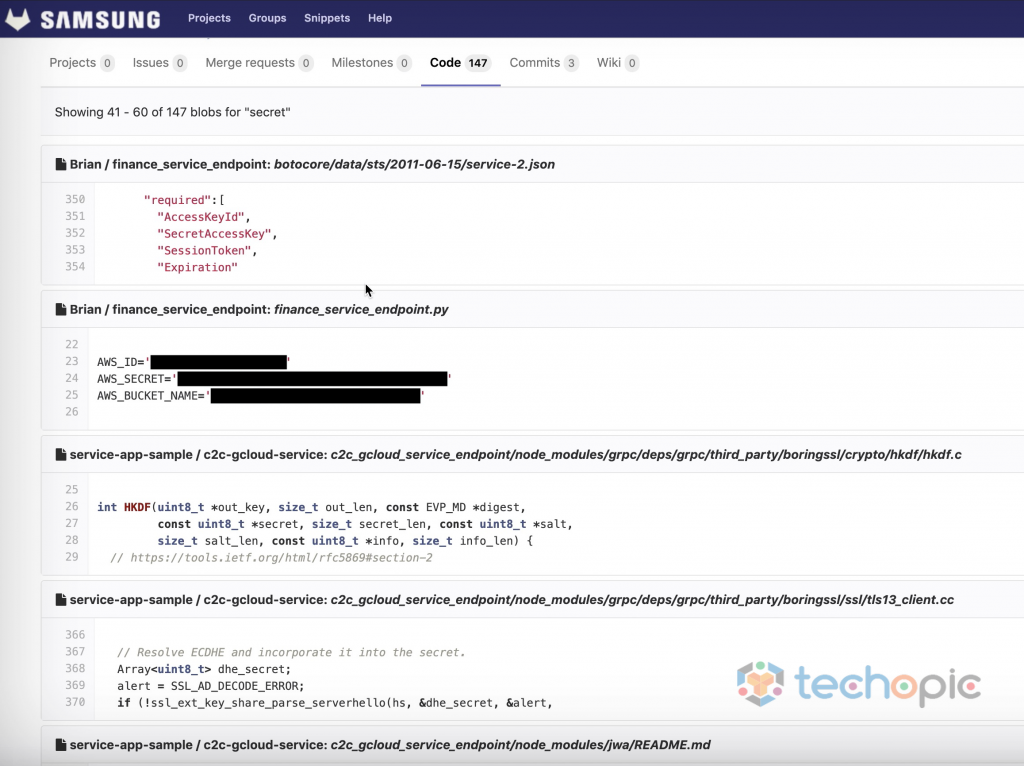
A development science lab employed by Samsung engineers was leaky sensitive ASCII text file, credentials and secret keys for many internal comes — as well as its SmartThings platform, a security investigator found.

A development science lab employed by Samsung engineers was leaky sensitive ASCII text file, credentials and secret keys for many internal comes — as well as its SmartThings platform, a security investigator found.
The physics big left dozens of internal writing comes on a GitLab instance hosted on a Samsung-owned domain, Vandev Lab. The instance, employed by workers to share and contribute code to varied Samsung apps, services and comes, was spilling information as a result of the comes were set to “public” and not properly protected with a countersign, permitting anyone to appear within at every project, access, and transfer the ASCII text file.
Mossab Hussein, a security investigator at Dubai-based cybersecurity firm SpiderSilk United Nations agency discovered the exposed files, same one project contained credentials that allowed access to the whole AWS account that was being employed, as well as over 100 S3 storage buckets that contained logs and analytics information.
Many of the folders, he said, contained logs and analytics information for Samsung’s SmartThings and Bixby services, however additionally many employees’ exposed non-public GitLab tokens hold on in plaintext, that allowed him to realize extra access from forty two public comes to a hundred thirty five comes, as well as several non-public comes.
Samsung told him a number of the files were for testing however Hussein challenged the claim, language ASCII text file found within the GitLab repository contained an equivalent code because the mechanical man app, revealed in Google Play on Gregorian calendar month ten.
The app, that has since been updated, has quite a hundred million installs so far.
“I had the non-public token of a user United Nations agency had full access to all or any a hundred thirty five comes on it GitLab,” he said, that might have allowed him to create code changes employing a staffer’s own account.
Hussein shared many screenshots and a video of his findings for TechCrunch to look at and verify.
The exposed GitLab instance additionally contained non-public certificates for Samsung’s SmartThings’ iOS and mechanical man apps.
Hussein additionally found many internal documents and slideshows among the exposed files.
“The real threat lies within the risk of somebody deed this level of access to the appliance ASCII text file, and injecting it with malicious code while not the corporate knowing,” he said.
Through exposed non-public keys and tokens, Hussein documented a huge quantity of access that if obtained by a malicious actor might are “disastrous,” he said.
Hussein, a white-hat hacker and information breach discoverer, according the findings to Samsung on Gregorian calendar month ten. within the days following, Samsung began revoking the AWS credentials however it’s not known if the remaining secret keys and certificates were revoked.
Samsung still hasn’t closed the case on Hussein’s vulnerability report, about to a month when he 1st disclosed the problem.
“Recently, a personal security investigator according a vulnerability through our security rewards program relating to one amongst our testing platforms,” Samsung exponent Zach Dugan told TechCrunch once reached before publication. “We quickly revoked all keys and certificates for the according testing platform and whereas we’ve nonetheless to search out proof that any external access occurred, we have a tendency to square measure presently investigation this any.”
Hussein same Samsung took till Gregorian calendar month thirty to revoke the GitLab non-public keys. Samsung additionally declined to answer specific queries we have a tendency to had and provided no proof that the Samsung-owned development atmosphere was for testing.
Hussein isn’t any interloper to coverage security vulnerabilities. He recently disclosed a vulnerable back-end information at Blind, AN anonymous social networking website in style among Silicon Valley workers — and located a server leaky a rolling list of user passwords for scientific journal big Elsevier.
Samsung’s information leak, he said, was his biggest realize so far.
“I haven’t seen an organization this massive handle their infrastructure victimisation weird practices like that,” he said.





